In today’s world most of the security incidents happen due to lack
of proper controls in the initial phases of product development. We
provide services and expertise to identify gaps and capabilities to
embed the controls in the software development lifecycle (SDLC).
This eventually helps our customers to speed up the product delivery
in a secure manner.
Highlighted below are some key secure software development services
and capabilities –
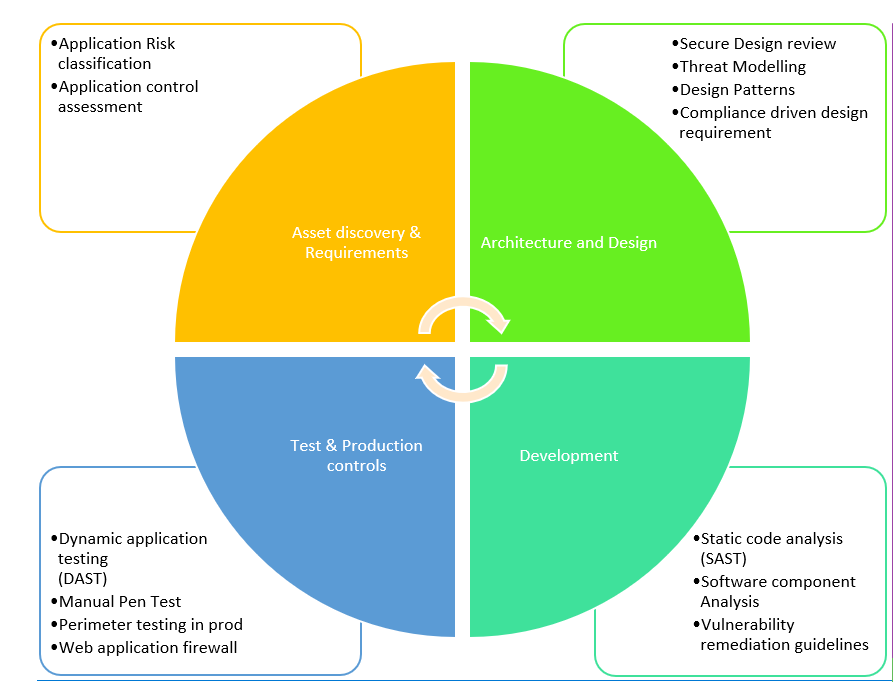
1. Asset Discovery and Requirements
– This is a key control to accurately identify the critical
applications and infrastructure, which defines the set of
controls that should be implemented to provide comprehensive
security. Our services works with the people and systems to draw
the mapping and develop the roadmap
a. Application risk classification
– The exercise identifies the key application specifics by
extracting the information from different sources and applies
an algorithm to classify the risk classification of the
application i.e. High, medium and low
b. Application control assessment
– As a subset of the control risk assessment, these services
perform a gap analysis of applications and infrastructures
based on the NIST and other security frameworks. We specialize
in identifying requirements that are compliance and country
driven
2. Architecture & Design
– This is a key control to accurately identify the critical
applications and infrastructure, which defines the set of
controls that should be implemented to provide comprehensive
security. Our services work with the people and systems to draw
the mapping and develop the roadmap
a. Secure Design Review
– Identifying design requirements and existing gaps in the
early phases of product development is key for building a
product with a futuristic design that improves performance and
scalability, while meeting all the security compliance
requirements. RiViv Consulting provides multiple options with
both automated design review and manual assessments that can
be seamlessly integrated with the CI-CD pipeline.
b. Threat Modeling
– RiViv Consulting conducts detailed manual threat modeling of
your applications and assets using different models such as
STRIDE and DREAD. We specialize in performing thread modeling
on cloud deployments such as AWS using some of the custom
developed techniques.
c. Design Patterns
– To effectively incorporate the standard, best security
practices in product development, often corporations rely on
key design patterns, RiViv Consulting has subject matter
experts that can work with technology architects and security
professionals to identify the key focus areas for
standardization and thereafter identify, develop and integrate
key secure design patterns.
d. Compliance driven design requirements
– We specialize in defining the compliance requirements that
help customers meet their diverse compliance and regulatory
needs, required to operate in various geographical locations
and help their global operations
3. Development
- We provide unique services to integrate key application
security controls as part of the CI/CD DevSecOps model. These
controls work in an automated fashion to identify OWASP Top 10
issues and defects and enables development teams to find issues
as they develop the code. Some of the key controls include –
a. Static application security testing (SAST)
– We can advise customers on different ways to integrate SAST
services with their SDLC. We further identify the end to end
process from scanning to vulnerability remediation by
designing the system integration to bug tracking tools such as
JIRA etc
b. Software Component Analysis (SCA)
– Similar to SAST, we advise our customers on the best ways to
integrate SCA/open source scanning tools as part of the SDLC.
Our services and approach are not just aligned with one of the
vendor solutions, instead our SME’s can help the security
teams integrate any of the chosen tools with the SDLC
c. Vulnerability remediation guidelines
– We provide resources and services to staff up the security
teams on vulnerability remediation activities. RiViv
Consulting works as an extension of the security teams or
independently to advise technology teams to understand the
identified issues and the best possible ways to address them.
We can further work with teams to create easily consumable
plug and play solutions that can be leveraged across multiple
teams for easy vulnerability remediation.
4. Test & production controls
– Application testing and implementing protection in the
production run-time environment is one of the key controls that
must be implemented as a first set of controls to identify
existing issues and apply necessary protection. RiViv Consulting
specializes in this area of application security and provides
following services:
a. Dynamic application security testing (DAST)
– One of the key controls in the secure SDLC is to perform
application security testing prior to the application features
being implemented in production. RiViv Consulting SMEs are
experienced testers with industry certifications and several
years of experience as pen testers. They are hands-on testers
that apply testing to the best practices and work with dev
teams to explore the end to end process of testing and
vulnerability remediation. These tests can be integrated with
the CI-CD pipeline to bring automated authentication scans as
part of the product delivery framework.
b. Manual Pen Test
– We provide specialized services to perform a detailed
penetration test. This is an authenticated test which uncovers
OWASP top 10 and covers following areas of application
functionalities -
- Authentication
- Authorization (privilege escalation)
- Session management
- Encryption and Data Handling
- Input validation
- Configuration management (insecure headers)
c. Perimeter Scan
– We provide capabilities to organizations to successfully
implement fully automated application security testing
controls in production. This specific testing is a lightweight
test that can perform authenticate or unauthenticated scans.
The issues are correlated with the DAST/Pen Test scans to
drive effective remediation.
d. Web Application Firewall (WAF)
– We provide SME capabilities to review the WAF rules and
advise our customers on how to implement customized WAF
policies for each application. The custom rules and
configurations are usually based on many factors including the
design, development and testing inefficiencies.